Preventing Data Loss Through Vigilant Server Configuration
In 2017, an ordinary day took an unexpected turn, highlighting the significance of diligent server configuration in safeguarding data. This story serves as a compelling reminder of the constant cybersecurity challenges that can arise in the digital world.
A NAS Setup
The story begins with a routine task: setting up a Network Attached Storage (NAS) solution for my family. The goal was straightforward—configure the NAS for optimal data storage. Little did I know that this venture into network management would soon become a real-world demonstration of the importance of server configuration.
An Unusual Notification
It all started with an unusual notification on my phone. The message indicated that my mom had accessed the NAS to make a file change, which was a rare occurrence. Typically, such access happened sporadically for essential backups of cherished photos and documents, and I was usually the one initiating these connections.
The situation grew more perplexing with a second notification stating that the connection had been abruptly terminated due to a policy violation. This unexpected turn of events prompted me to investigate further.
A Cyber Intrusion Unfolds
Upon entering my mom’s office, I was greeted by an unfamiliar graphical user interface on her computer—a sight I had only seen in screenshots. It raised questions: How had this unexpected software intrusion occurred? What was its intent, and what data was at risk?
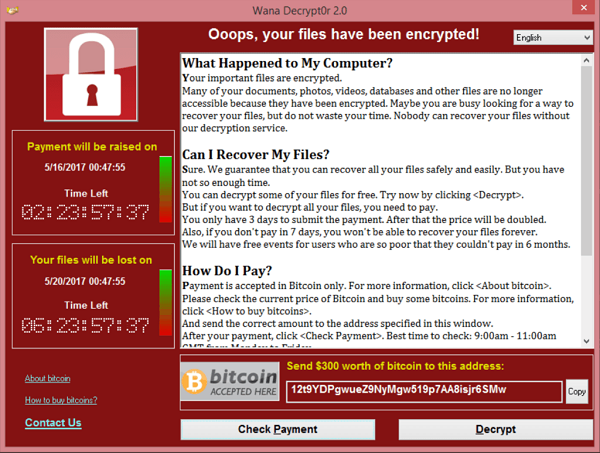
My concern deepened when I realized that the ransomware had managed to open an SMB connection to the NAS using her login credentials. It raised the possibility that the NAS had already been a potential target.
Swift Action and Server Configuration
Despite the unexpected situation, I chose to act swiftly. Drawing upon my knowledge of cybersecurity, I set out to identify and isolate the threat. Recognizing that time was of the essence, I reviewed the server’s configuration.
I had configured the NAS to monitor file changes diligently. Any rapid alterations to files would trigger an alert, potentially preventing extensive damage. This precautionary measure turned out to be pivotal.
Containment and Data Protection
As minutes ticked by, the ransomware’s impact became evident—it had locked down approximately 50 files on my mom’s computer. However, thanks to the rapid detection and containment on the NAS, the damage was contained. Most importantly, the vast majority of our valuable data, consisting of thousands of files, remained secure and unharmed.
The Lessons Learned
This cybersecurity incident, though unexpected, reinforced the significance of proper server configuration in safeguarding data. It highlighted the need for vigilance, even during routine tasks. Cyber threats can manifest unexpectedly, emphasizing the importance of preparedness.
While the origin of the malicious file on my mom’s computer remained a mystery, this experience underscored the critical role of cybersecurity in protecting data and the broader digital environment. It was a practical demonstration of how vigilant server configuration can prevent data loss during unforeseen cyber threats.